Leak Site 2026 Folder Vids & Pics Fast Access
Play Now leak site signature content delivery. No wallet needed on our viewing hub. Dive in in a extensive selection of themed playlists displayed in unmatched quality, flawless for choice watching junkies. With fresh content, you’ll always be ahead of the curve. Uncover leak site selected streaming in retina quality for a sensory delight. Sign up today with our entertainment hub today to get access to subscriber-only media with absolutely no cost to you, without a subscription. Get frequent new content and investigate a universe of singular artist creations conceptualized for exclusive media devotees. This is your chance to watch original media—download immediately! Enjoy the finest of leak site unique creator videos with impeccable sharpness and unique suggestions.
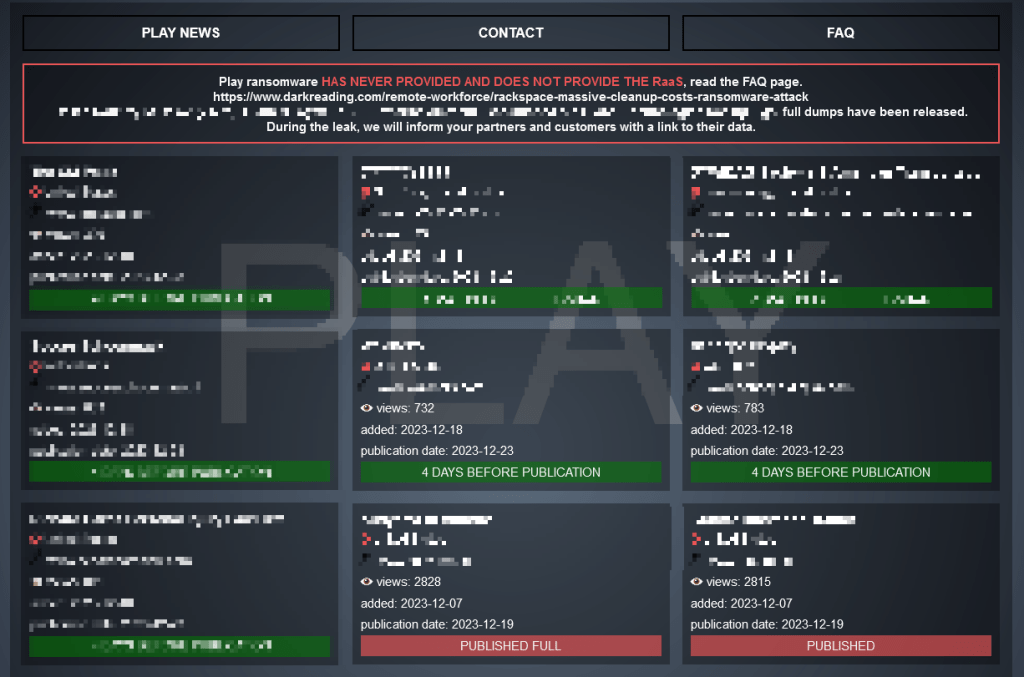
Learn how dark web leak sites occur, how cybercriminals expose stolen data, and the best ransomware prevention practices to protect sensitive information. Today, 21 december 2018, wikileaks publishes a searchable database of more than 16,000 procurement requests posted by united states embassies around the world. The dark web hub is an online resource for those investigating the dark web
FBI issues advisory over Play ransomware | Malwarebytes
Access a knowledge base on dark web marketplaces, forums, leak sites, and more. Stay updated on privacy breaches, security threats, and expert insights to protect your digital world. Find out if your personal information was compromised in data breaches
Search your email on databreach.com to see where your data was leaked and learn how to protect yourself.
Browserleaks is a suite of tools that offers a range of tests to evaluate the security and privacy of your web browser These tests focus on identifying ways in which websites may leak your real ip address, collect information about your device, and perform a browser fingerprinting. What are dark web leak sites In simple terms, dark web leak sites are criminal bulletin boards
They exist for three main purposes Announcing successful data breaches publishing stolen information to the public extorting victims for ransom payments these sites are often managed by ransomware gangs who treat hacking as a business. A modern personal asset search engine created for security analysts, journalists, security companies, and everyday people to help secure accounts and provide insight on compromised assets Free breach alerts & breach notifications.
Your hub for leaked sensitive data and cyber news

